 I have
been playing around with OpenID recently and considering its significance. OpenID
offers a "single digital identity .. you can login to all your favourite websites", and its adoption is rapidly
accelerating especially since services like Yahoo and Blogger have added OpenID support to the many millions of
existing user accounts.
I have
been playing around with OpenID recently and considering its significance. OpenID
offers a "single digital identity .. you can login to all your favourite websites", and its adoption is rapidly
accelerating especially since services like Yahoo and Blogger have added OpenID support to the many millions of
existing user accounts.Maybe I'm missing something here, but I am surprised by the lack of attention OpenID is getting in the enterprise context.
And when it is considered, it is often as an either/or proposition. As Nishant Kaushik writes in his excellent identity blog:
.. simple web applications with minimal needs could get away with simply supporting OpenID. But that should not be confused with not requiring a full-fledged identity services infrastructure where appropriate.I think this is somewhat misdirected; certainly not the whole story. OpenID-enabling existing applications for an external audience is already a trivial exercise. It's a simple API, and plugins or toolkits are available for most programming environments. I think the much bigger deal is looking at OpenID from the opposite perspective - using enterprise security infrastructure to support OpenID authentication.
In my view, OpenID is key to unlocking the true potential of "Enterprise 2.0", which is what I wanted to discuss here to try and explain my thoughts and get some feedback.
It may also lead us to think more clearly about what Enterprise 2.0 really is. This is the current definition up on wikipedia:
Enterprise social software, also known as Enterprise 2.0, is a term describing social software used in "enterprise" (business) contexts..The "social" nature of Web 2.0 tends to get the headlines, and hence by simple transference must be to basis of Enterprise 2.0. Right?
However, I'm not convinced.
Expecting Enterprise 2.0 success by simply adopting social networking features of Web 2.0 just seems a little naive. For a start, it implies and requires phenomenal change in the social and organisational fabric of a company to get off the ground, and there is no guarantee the benefits will be worth the pain of change. In many organisations it may just be too much, too soon, and fail completely.
Much as I love them, I don't even think "mashups" will be the killer app for Enterprise 2.0.
I think the key is a much more mundane aspect of Web 2.0 that gets lost in the facebook frenzy: the simple fact that users are being exposed to just so darn many useful tools in the ever increasing range of web applications (or Rich Internet Applications aka RIA).
We see unprecedented utility in the applications on offer, approaching what we expect from desktop or dedicated applications. And there is an incredibly low barrier to participation - you can sign-up within a minute and with usually no immediate associated cost.
So my main proposition is that the quick win for Enterprise 2.0 is for companies exploit the RIA boom. Spend your time figuring out how to exploit the burgeoning Web Application offerings. Do NOT waste your time scheming how to clamp down on usage, or on replicating the tools yourself.
The real and immediate benefits include reduced IT spend, better utility and happier users .. and set the stage for moving to the world of "Advanced Enterprise 2.0" with mashups and social networking for example.
The caveat of course is that the enterprise must ensure that matters of availability, data protection, confidentiality and privacy are not compromised in making such a move.
But this presents a dilemma for the enterprise. A tough choice between undesirable outcomes:
- ban and fore-go the benefits of adopting external Web Applications for enterprise use;
-
- allow their use, but lose control of the data, identities and secondary use derived from using such applications;
-
- or be faced with re-implementing all those cool features within the firewall (and risk becoming disconnected from the external audience).
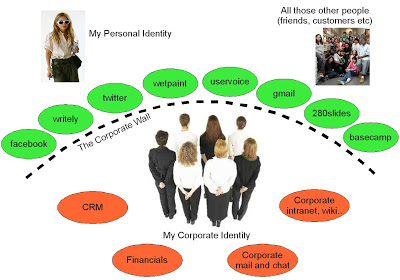
This leads us to the present state-of-the-art in Enterprise 2.0, which must necessarily work around the constraints of the corporate boundary.
-
- Some companies are adopting External Web Applications where they address a largely external audience (a good example is the official Oracle Wiki which runs on wetpaint). But here they remain disconnected from internal systems.
-
- For internal adoption of Web 2.0 technology, IT departments are often re-implementing all the cool stuff inside
the firewall.
The CEO wants a blog? Customer support want to setup a wiki? Sure, we can install it. Where install means friggin' around for a few months to select and acquire the software, integrate it with the standard enterprise security/monitoring/hosting/blah environment, customise it to the corporate branding etc etc.
And I think it denies the dirty little secret that I bet exists in most organisation: your employees are already using these services for business purposes!
Using a personal credential for business purposes on an external service (whether OpenID or not) presents a whole range of challenges:
-
- It is a provisioning nightmare. What happens when the employee leaves? The company doesn't control the account, so it can't be disabled. Whether you can remove access from any corporate data held in the external service depends totally on the application itself and how it was setup.
-
- For the individual, there is a concern about keeping their professional and private lives appropriately separated. Too easy for your tweets to end up in the wrong hands in the wrong context.
-
In other words, the key to all of this IDENTITY.
Imagine for a moment the ideal world. I would have a corporate identity that works transparently within the enterprise and also for useful external services. And I could keep this quite separate from my personal identity (even though I may use some of the same external services on my own time).
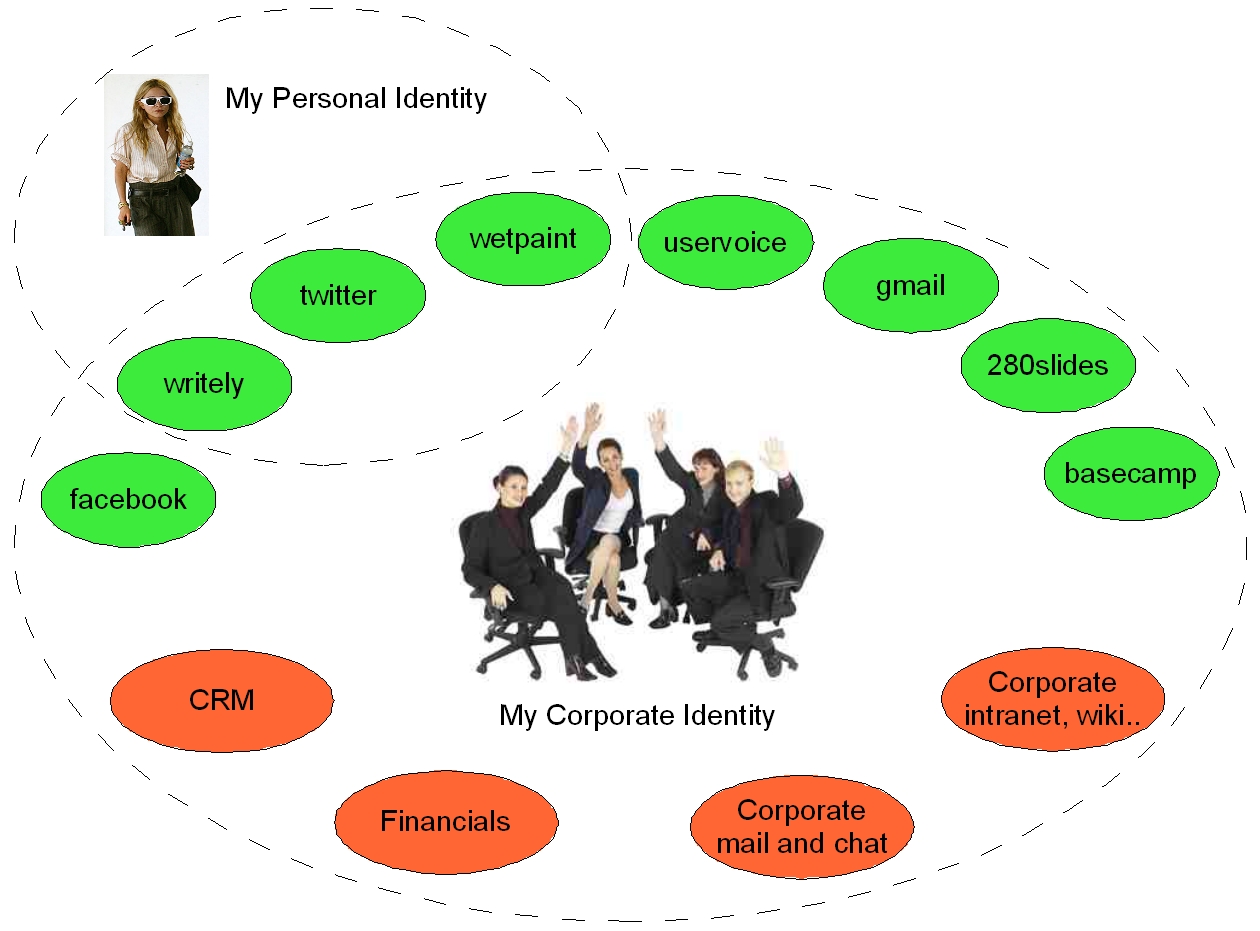
The question now is whether we are far from being able to achieve this? I think not...
The call to Enterprise Identity Management Stack providers..
That means Microsoft, Oracle, IBM, Sun and so on.. the companies that produce the security software that is managing your enterprise identity every time you sign in to an enterprise application.Many of these guys are members of the OpenID Foundation, but on the whole it is hard to find clear statements of direction at the moment, and the initial focus has been around demonstrations of how they can use credentials from other OpenID providers.
We need to see two things in particular:
- OpenID provider support in their core identity management stacks, so that enterprise credentials can be used as OpenID credentials under the control of the company (e.g. they can be disabled when the employee leaves). Call that part of a "Service Oriented Security" strategy if you like, just make the option available;-)
-
- Include that ability to blacklist/whitelist sites that the credentials can be used for.
There will always be good reasons why certain Web Applications may be off limits for corporate use. For example, a law firm may not be able to use Google Documents because of jurisdictional concerns.
Dion Hinchcliffe presented the case well in the recent article "openid: The once and future enterprise Single Sign-On?", along with a great visualisation:
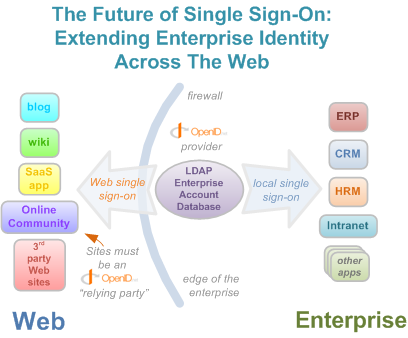
The call to Web Application providers..
Firstly, the big guys like Yahoo! need to support third party OpenID credentials. This seemed to be the main thrust of Hinchcliffe's article. I hope this is just a matter of maturity and not business model pig-headedness, but to offer OpenID sign-in only if your OpenID provider is the same company is not really in the right spirit of things!More generally applicable however is a major consideration for any Web Application provider that wants to target the enterprise market: addressing the security issue with OpenID support only opens the door. To step through, you must be ready to meet the specific demands of an enterprise customer.
First of these must be data ownership. I didn't want to focus on it in this post because I think it is an orthogonal concern to security. But if you want enterprise customers, be prepared to to consider requirements such as:
- Access to all data owned by the company's users on the service. For backup, export, and analytics.
-
- Audit and compliance
-
- Service levels
The call to Enterprise Software vendors..
The idea of a "Web 2.0 appliance" is I think very attractive to many organisations: an easy on-ramp to the space without the need to build up a whole range of specialist skills within the company. In the appliance category I would include Oracle WebCenter and the new IBM Mashup Center. Needing OpenID authentication support in these products is of course a no-brainer in order for them to have appeal in cases where you wish to mix internal and external user audiences.Enterprise Software vendors need to go further however. The enterprise of the future, which expects to operate seamlessly on the web, will need the ability to "export" corporate identity to the world. Right now, that means capabilities like having OpenID provider support in your Enterprise Identity Management services.
Given the state of consolidation in the industry however, OpenID may present a dilemma for vendors who are faced with the prospect of OpenID support in their Identity Management stack cannibalizing sales of their application suites, as users start to exploit external Web Applications.
But to be recalcitrant and stand against the move to OpenID will only accelerate the onset of a winner-takes-all showdown in the enterprise applications market.
Personally, I believe the showdown is inevitable: with the combined pressures of RIAs, cloud computing, oligopolistic pricing and increasingly sophisticated open source alternatives, I think it is quite likely we will see the enterprise software market go supernova within the next 5 years i.e. blow itself to pieces after a few more years of consolidation ... but that's a topic for another post perhaps;-)
The enteprise software vendors that survive will be the ones who truly embrace being open, and that includes OpenID.
Conclusions?
Well, I wonder if I've convinced anyone?To me it seems that the ability for enterprises to add OpenID provider support to their security infrastructure will be the key to unlocking the full potential of Enterprise 2.0.
Until such a facility is available from the mainstream Identity Management vendors, we will just be messing around on the fringe.
NB: edited for clarity 9-Sep-2008